I’ve been arguing for years that we in information security aren’t doing anyone any favors when we demand that people use for passwords something impossible to remember, then we demand that they remember it, and then we insist that, for God’s sake, they never write it down.
And as if we weren’t bad enough, soon regulators came along and made it worse: “Rotate your passwords every 90 days,” they sagely intoned, “to make them more secure.”
They’re wrong.
Forced password rotation, or password expiry, is just a big stupid thing to do. The problem now is convincing auditors that you’re OK to stop doing it — overcoming dogmatic adherence to a dumb thing is not easy.
But it’s possible.
Here’s how to justify Password-Expiry-Only-on-Suspicion-of-Compromise to your auditors:
Let Me Sum Up:
NIST Special Publication 800–63B guidance
National Cyber Security Center guidance
How I Got Here
The topic came up for me again recently when revamping the information security program at a financial institution. This is a place that has gone to some pretty reasonable lengths to protect themselves: They know who their users are, and what they are permitted to do, on what devices, with what configurations, from which locations. They’ve got well-managed machines, and Single-Sign On, and they require push or XOTP-based second-factor authentication for everything they use. And sometimes, they require something you know, and two things you have.
And now, here was a regulator asking them to audit regularly not just what was accessed, and when, and by whom, and whether each user was Kosher, but also, the last time the person’s password was changed.
You know, for security.
The chief engineer was incredulous. “Rotate passwords? We get a new password every time.”
And even if we didn’t — even if we just had single-factor — rotating passwords is just … Stupid.
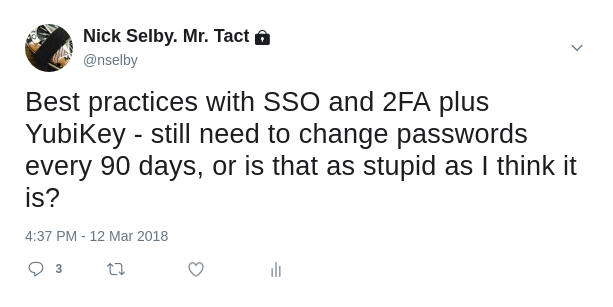
As I often do when I’m apoplectic, I tweeted.
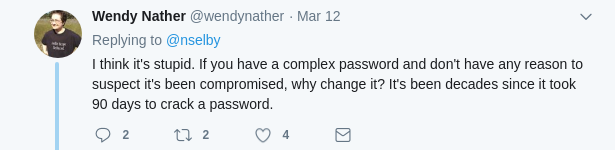
And, lo! wisdom arrives minutes later from @wendynather:
Homeopathy for your Network
The argument about whether changing passwords is more secure is also far less established scientific fact than simple common belief. Researchers at the School of Computer Science, Carlton University, Ottawa, state that
“The historical idea is that [regular password changes] increases security — although the implied gain has never been quantified.”
Rotating passwords: an expensive placebo security measure.
Indeed, the disruption, and the number of man-hours wasted and user frustration as they need to do password resets associated with their needless password updates make this exercise a significant disruption to our business with no evidence of increased security.
It is simply expensive effort to achieve a placebo security measure. It’s homeopathic enterprise security. It’s the TSA for your network.
I’ll go you one farther: I argue that not changing the static password is more secure than changing it every 90 days.
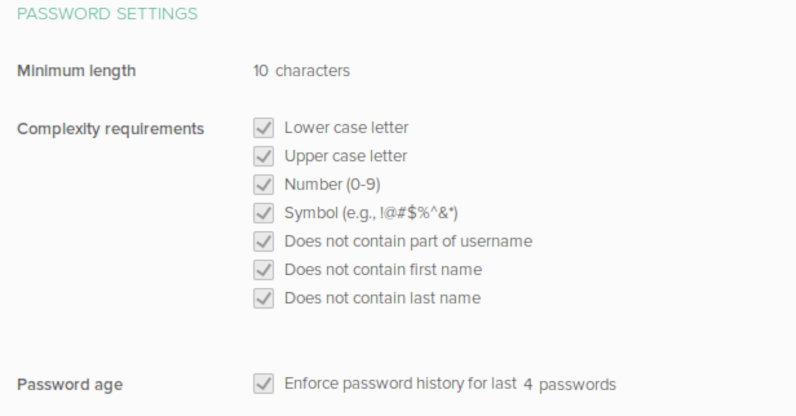
That’s because if — like ours — the static password is strong and secure (in our case, it uses at least ten characters that must include mixed upper and lower case, and at least one number and one special character), then forcing users to remember another such inherently un-memorable password actually encourages bad practices such as re-using old passwords, making predictable variations from existing passwords, or writing them down.
This is not a crazy idea, or one that is out of left field. It’s certainly not original. And it’s taking hold in some pretty conservative places.
In 2016, Lorrie Cranor, Chief Technologist of the Federal Trade Commission wrote in an official FTC publication,
“there is a lot of evidence to suggest that users who are required to change their passwords frequently select weaker passwords to begin with, and then change them in predictable ways that attackers can guess easily. Unless there is reason to believe a password has been compromised or shared, requiring regular password changes may actually do more harm than good in some cases.”
Then Chris Swan tweeted something that would make my life significantly better:

Chris (if you don’t know him you should, because it is nice to have at least one friend who lives five years in the future) is talking about NIST Special Publication 800–63B guidance in Section 5.1.1.2, “Memorized Secret Verifiers” — that’s “password” to you:
“Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.” [Emphasis in original]
A year earlier, the UK Government’s National Cyber Security Centre reached the same conclusion, saying,
“Only ask users to change their passwords on indication of suspicion of compromise.”
Chris pointed me to a great article by Graham Chastney, a technologist at Chris’ firm, DXC, that Chastney wrote when the UK NCSC (then CESG) guidance mentioned above came out.
That article is worth a read, but don’t miss a nice related piece on Chastney’s personal blog, The Four Ages Of Remembering a New Password.
Regulators
Oh, by the way: when dealing with regulators we speak with, it’s nice to deal with woke ones. When I ran all this by them, I was delighted to see that they agreed, and that they had already formed a position on the matter:
“[We are] in fact familiar with the NIST guidance which you are citing. While we still do recommend that passwords be changed periodically we no longer require such changes to be made on a routine basis.”
As the kids a generation ago used to say, “Boo-ya.”
Unless you’re dealing with PCI-DSS. I’d argue the above is a compensating control for their particular brand of jackassery, and would have hoped that any reasonable auditor would recognize that — did you see what I did there, using the word “reasonable” and the acronym “PCI-DSS” within 100 feet of one another? — but to paraphrase Dan, it’s hard not to suck deep, deep down when you are PCI-DSS.